Azure Key Vault Retention Policy
Azure Key Vaults now enforce a Soft-Delete feature to prevent accidental deletion. This post discusses how to use Policy to control the associated retention period.

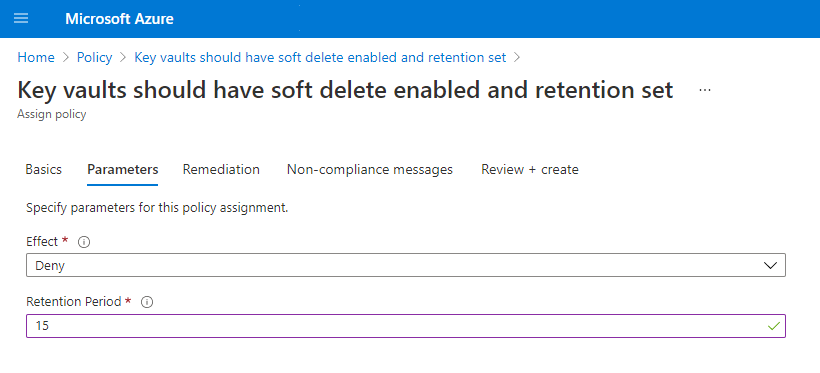
This custom Azure Policy, as shown below, can be assigned and set to “Deny” to stop Vaults being created without the chosen retention time being set. In this example the policy was assigned with a value of 15 days.
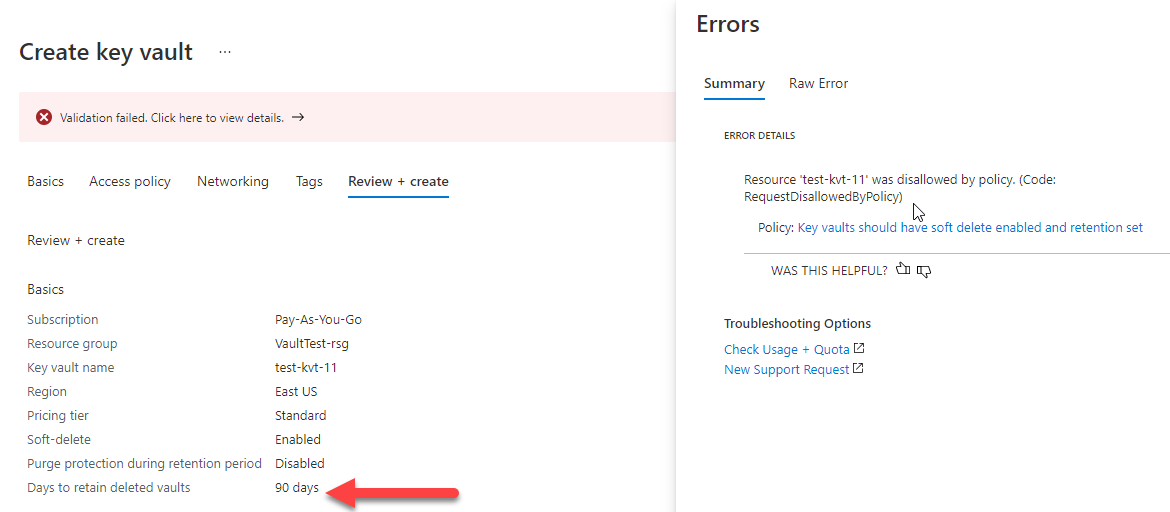
With the Policy assigned, if a Key Vault is created with a different value, for example the default 90 days, the creation will be blocked. This block happens at the “Review and Create” stage in the Azure Portal:
And will be similarly enforced when using PowerShell as follows:
1PS /home/chris> New-AzKeyVault -ResourceGroupName "VaultTest-rsg" `
2 -Name "test-kvt-11" `
3 -Location "eastus" `
4 -SoftDeleteRetentionInDays 90
5New-AzKeyVault: Resource 'test-kvt-11' was disallowed by policy.
6 Reasons: 'The soft-delete retention on Vaults must be set to 15 days'.
7 See error details for policy resource IDs.
Sample Policy
1{
2 "properties": {
3 "displayName": "Key vaults should have soft delete enabled and retention set",
4 "policyType": "Custom",
5 "mode": "Indexed",
6 "description": "Deleting a key vault without soft delete enabled permanently deletes all secrets, keys, and certificates stored in the key vault. Accidental deletion of a key vault can lead to permanent data loss. Soft delete allows you to recover an accidently deleted key vault for a retention period configured to a provided number of days. ",
7 "metadata": {
8 "category": "Key Vault",
9 "updatedBy": null,
10 "updatedOn": null
11 },
12 "parameters": {
13 "effect": {
14 "type": "String",
15 "metadata": {
16 "displayName": "Effect",
17 "description": "Enable or disable the execution of the policy"
18 },
19 "allowedValues": [
20 "Audit",
21 "Deny",
22 "Disabled"
23 ],
24 "defaultValue": "Audit"
25 },
26 "retentionTime": {
27 "type": "Integer",
28 "metadata": {
29 "displayName": "Retention Period",
30 "description": "Number of days to retain Vault in Soft Delete"
31 },
32 "defaultValue": 90
33 }
34 },
35 "policyRule": {
36 "if": {
37 "allOf": [
38 {
39 "field": "type",
40 "equals": "Microsoft.KeyVault/vaults"
41 },
42 {
43 "anyOf": [
44 {
45 "field": "Microsoft.KeyVault/vaults/enableSoftDelete",
46 "exists": "false"
47 },
48 {
49 "field": "Microsoft.KeyVault/vaults/enableSoftDelete",
50 "equals": "false"
51 },
52 {
53 "field": "Microsoft.KeyVault/vaults/softDeleteRetentionInDays",
54 "notEquals": "[parameters('retentionTime')]"
55 }
56 ]
57 }
58 ]
59 },
60 "then": {
61 "effect": "[parameters('effect')]"
62 }
63 }
64 }
65}