Home Lab VPN Connection
I wanted to be able to connect to my new home lab from off-premises (that’s a technical way of saying “when I’m not at home”). My solution to this was to setup an Ubuntu VM running OpenVPN, following the comprehensive instructions here and configuring my home broadband router to forward UDP port 1194 to the VM.
Whilst this looked great, when I got offsite and tried to connect back in I couldn’t get to my ESXi host. Connections to the VM hosting the VPN were fine; I could connect and then ping/SSH the VM (and I was also routing SSH to that VM on my home router- that also worked) but anything beyond that- the rest of my home network- was inaccessible.
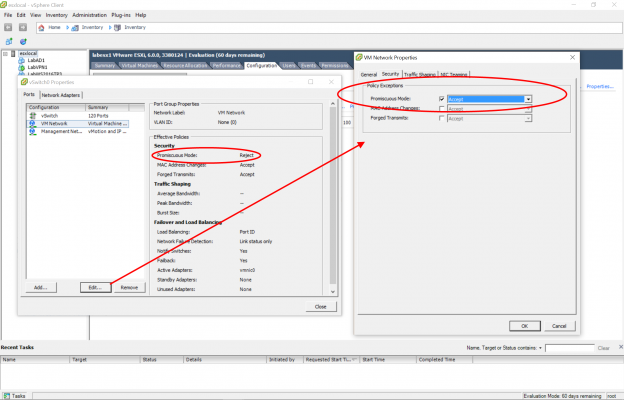
After some digging, this post pointed me to the probable solution. The Virtual Switch that sat in ESX between the router and the VPN server was set by default to reject promiscuous packets, so packets being sent to the VPN for it to route were never reaching the VM.
So, armed with a possible solution I set about trying to fix it remotely. I can’t open the vSphere client to enable promiscuous mode because the VPN isn’t letting me through. The physical host is now sitting headless at home, and I’m not, so I can’t sit in front of the console. Luckily (and thanks to a colleague for reminding me this) I had that SSH routing enabled, I can turn off the VPN and fall back on an SSH tunnel to make the connection using Putty on my off-site workstation.
So next I tried a normal SSH tunnel to port 443 on the ESXi host. This didn’t work beyond the web browser, and a bit more digging suggested I needed ports 902 and 903 as well. Not a problem, PuTTY lets us port forward several ports simultaneously. However, that was still unsuccessful- if I tried to connect to 127.0.0.1 from the vSphere Client on my Windows laptop it failed.
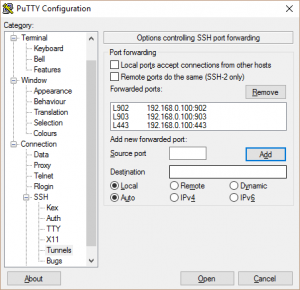
More digging (it’s one of those days where I don’t know where I’d be without Google) and I found this post by Anthony Eden. It turns out that I need to put an entry in my local hosts file on Windows pointing at 127.0.0.1. This worked, bizarrely, and I could now open up the vSphere Client and connect to my home lab.
Next step was to set that promiscuous mode on the vSwitch, this is a straightforward operation and whilst it does open up VM traffic across that switch to certain vulnerabilities, it solved the problem and I’m not planning on running a major finance appliance storing lots of personal data on this rig anyway, and I’m anticipating most applications I try will be separated by further switching as well.
With the VPN running I can now connect to both the ESXi host itself and any Virtual Machines within the environment.
So, setting up the VPN on my Home Lab was not quite as straightforward as I’d originally hoped, but I got there in the end. I can now sit in the office at lunchtime and call this my infrastructure in the cloud. To summarise for anyone trying to do the same thing.
- Create an Ubuntu Linux VM with a static (or reserved) IP Address
- Install OpenVPN following the instructions here
- On the vSwitch attached to the VM enable promiscuous mode
- On your broadband router forward port 1194 to the IP address of the VM
- Install the OpenVPN client on your laptop, go off-premises, and test.